Microsoft Auto-enrollment Operations
ENTERPRISE This is an EJBCA Enterprise feature.
The following provides an overview of how to configure auto-enrollment in EJBCA.
For an example guide of setting up MS Auto-enrollment, see the Microsoft Auto-enrollment Configuration Guide and for a conceptual overview, see Microsoft Auto-enrollment Overview.
To configure auto-enrollment, click Autoenrollment Configuration in the EJBCA menu
Auto-enrollment configuration is based on aliases and each alias is configured on the Manage Autoenrollment Aliases page.
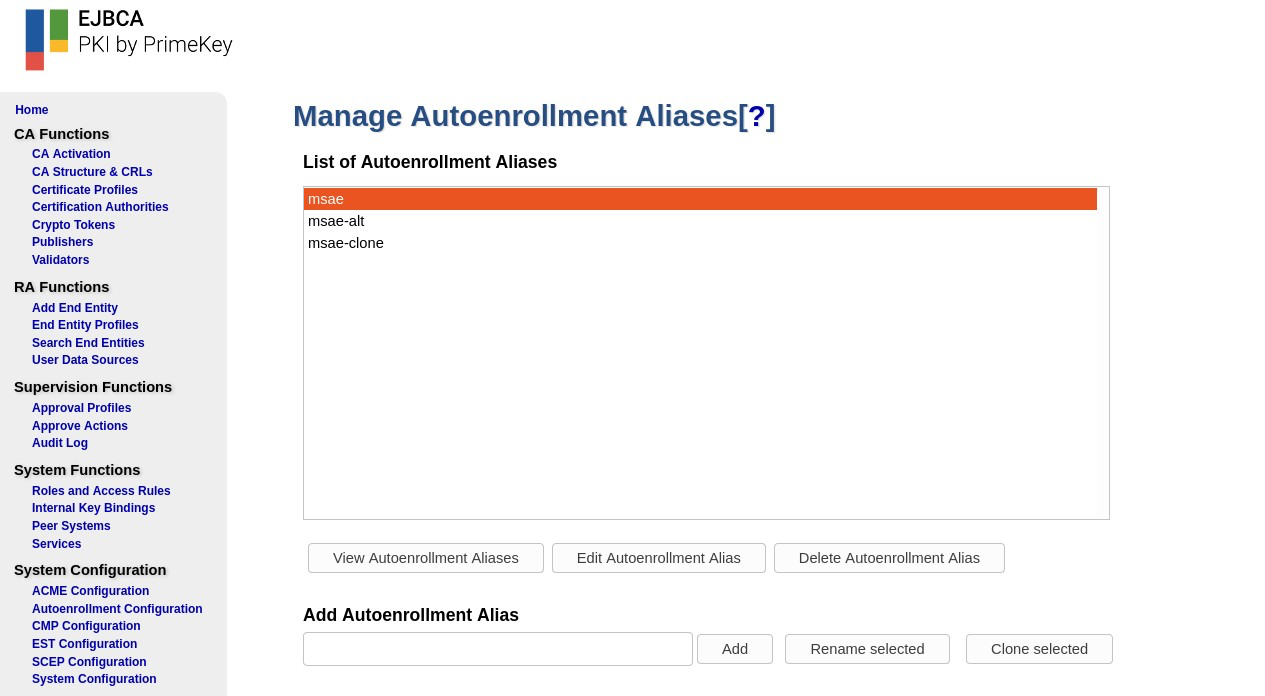
To add a new alias, specify a name for the alias, click Add and then select Edit Autoenrollment Alias.
Configuring Domain and Connection Settings
The following sections cover the Domain and Connection configuration settings.
Domain Controller and Policies Settings
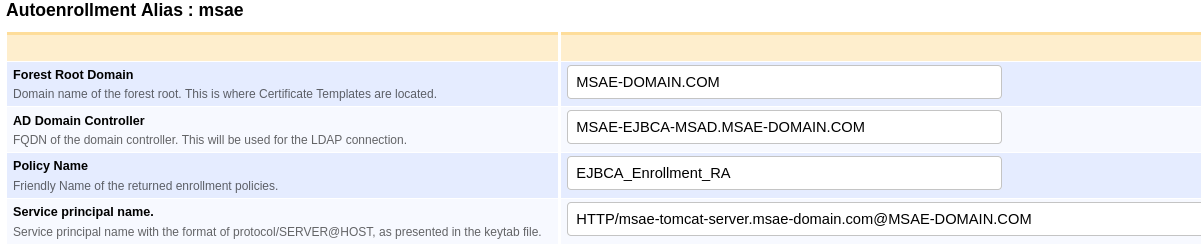
The following displays the settings on the Autoenrollment Alias configuration page.
|
Field |
Desctiption |
|
Forest Root Domain |
Domain name (DN) of the forest root (the location of the Certificate Templates). |
|
AD Domain Controller |
Fully qualified domain name (FQDN) of the domain controller (used for the LDAP connection). |
|
Policy Name |
Display name of the Certificate Enrollment Policy retrieved by clients (free text). |
|
Service Principal Name |
Service principal name in the format protocol/SERVER@HOST. |
Kerberos Settings
The following displays the Kerberos settings on the Autoenrollment Alias configuration page.
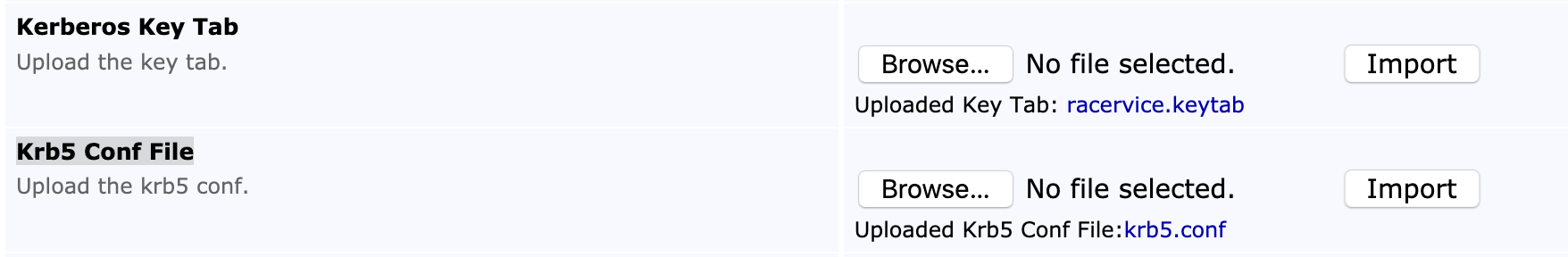
Import the Key Tab and the configuration file using the following fields.
|
Field |
Description |
|
Kerberos Key Tab |
Import a valid key tab file. |
|
Krb5 Conf File |
Import a valid krb5.conf file. |
Configure AD Connection
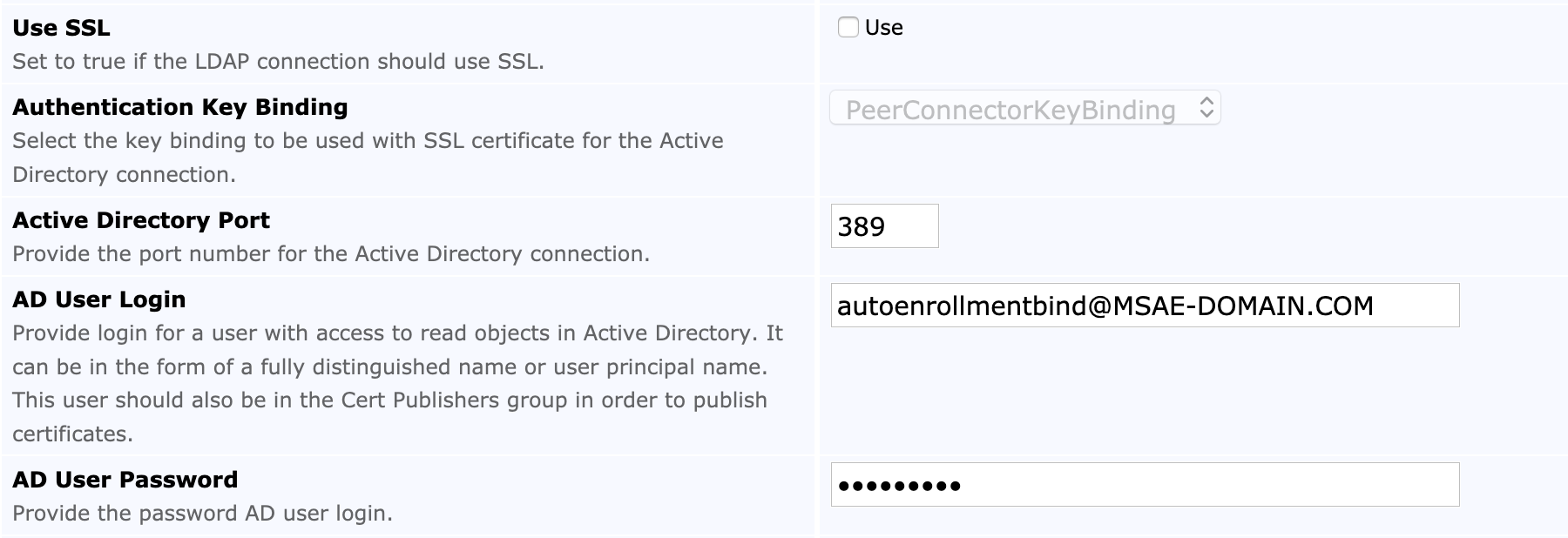
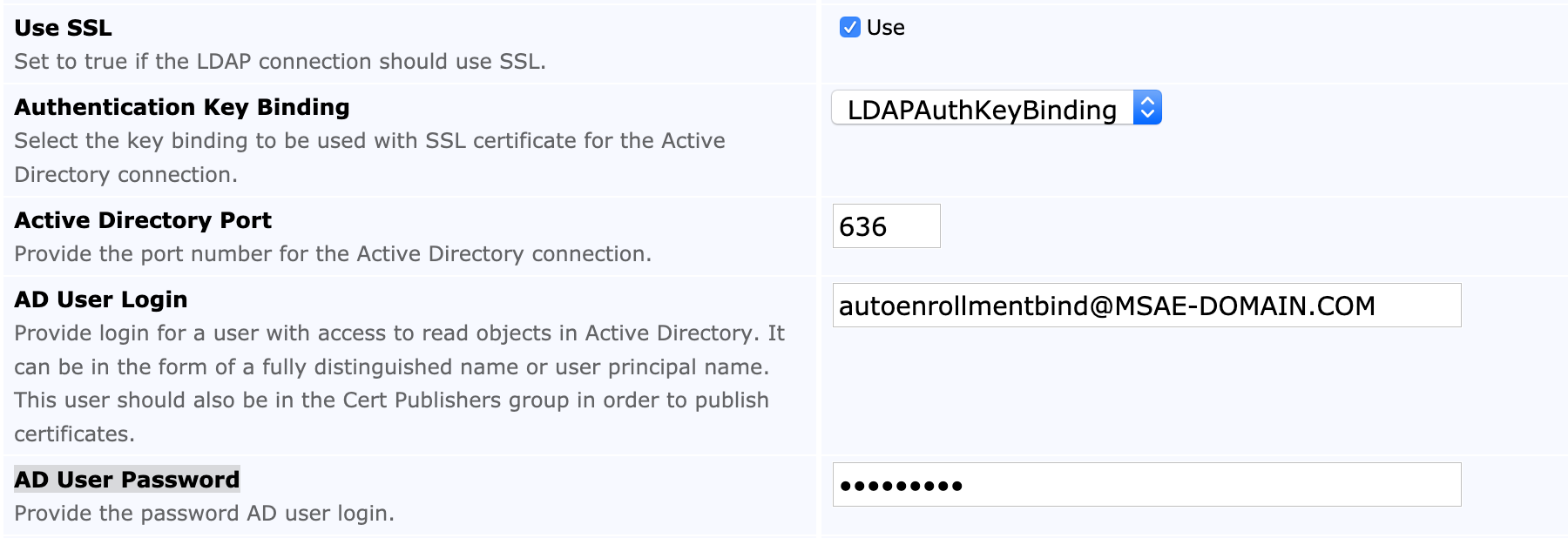
The following fields are set for the Active Directory (AD) connection. Note that SSL can optionally be used for the EJBCA instance's connection to the LDAP server.
|
Field |
Settings Without SSL |
Settings Using SSL |
|
Use SSL |
Cleared |
Selected |
|
Authentication Key Binding |
Disabled |
Select Relevant Key Binding |
|
Active Directory Port |
389 (or port for your LDAP connection) |
636 (or port for your SSL LDAP connection) |
|
AD User Login |
user@DOMAIN.COM |
user@DOMAIN.COM |
|
AD User Password |
your password |
your password |
The Active Directory bind account (AD User Login) can be provided in any of the following formats:
"autoenrollmentbind@yourcompany.com" (sAMAccountName followed by @, followed by either DNS name of a domain in the same forest or a value in the uPNSuffixes of the Partitions container in the config NC replica)
CN=autoenrollment bind,CN=Users,DC=yourcompany,DC=com" (Full DN)
autoenrollment bind" (Display Name)
EJBCA instance's connection to the LDAP server can be over SSL if specified. Once the Use SSL option is selected, an Authentication Key Binding can be specified. The selected key binding is used as a trust entry for the LDAP SSL certificate. For details on creating the binding needed for the SSL connection, see Setting up an Authentication Key Binding.
The following displays the settings for AD connection without SSL:
The following displays the settings for AD connection with SSL:
Configure Default CA
The default CA used for auto-enrollment is selected using the Default CA field.

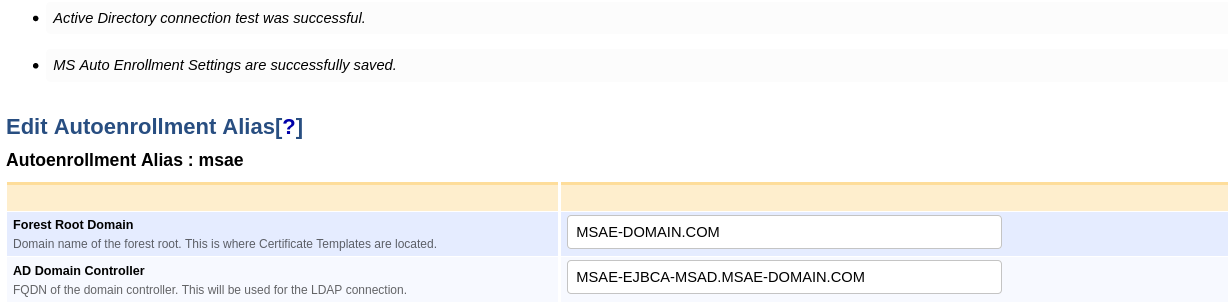
Once the configuration has been stored by clicking Save, the AD connection can be tested by clicking Test Connection.
A successful connection will show the following message:
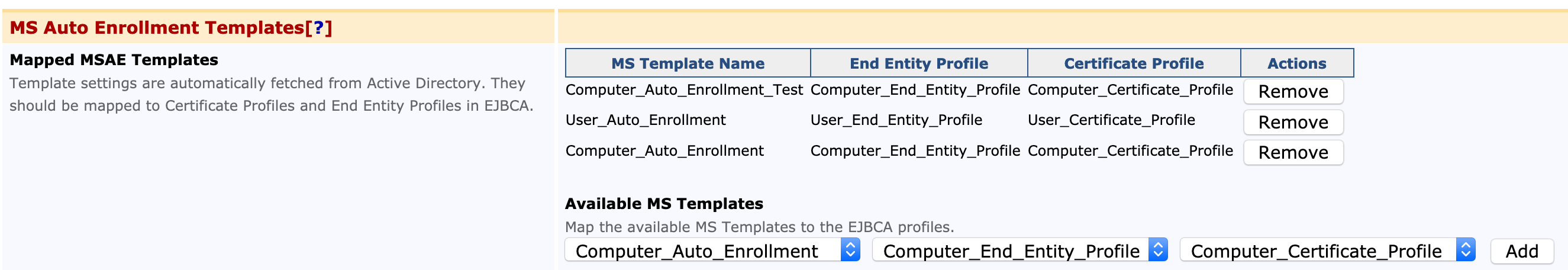
Configuring Microsoft Auto-enrollment Templates
In order to enroll through Microsoft Auto-enrollment, the Microsoft Templates are mapped to End Entity Profiles and Certificate Profiles.
In the Available MS Templates section, select a Template, an End Entity Profile and a Certificate Profile and click Add.
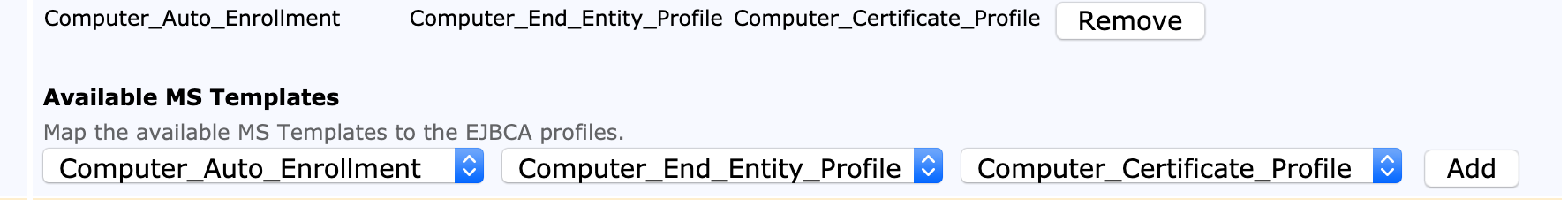
Added template mappings are added and listed as Mapped MSAE Templates.